A new vulnerability in mac OS allows an attacker to remotely execute commands
The researcher found a bug in the Mac OS Finder that allows an attacker to run commands on Mac computers with any version of macOS (up to the latest version of Big Sur). There is no patch for this problem yet.

The vulnerability was discovered by an independent information security expert Park Minchan, and it is related to how mac OS processes .inetloc (Internet location files) files. .inetloc files are system-wide bookmarks that can be used to open various network resources (news://, ftp://, afp://) and local files (file://). As a result, these files force the OS to run any commands embedded by the attacker, without any warnings or requests.
"Such files can be embedded in emails that, and if the user clicks on them, they will execute embedded commands, without displaying a hint or warning," SSD Secure Disclosure warns.
Although Apple tried to fix the problem without assigning a CVE identifier to the vulnerability, Minchan noticed that the company's patch only partially fixed the problem, and the vulnerability can still be exploited by changing the protocol used to execute embedded commands from file:// to FiLe://.
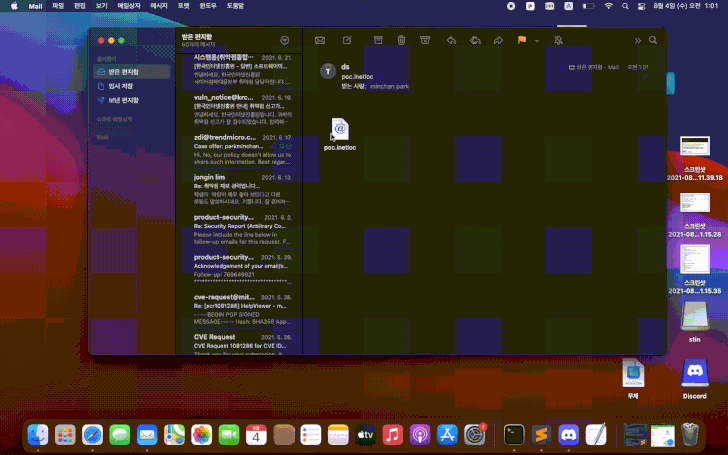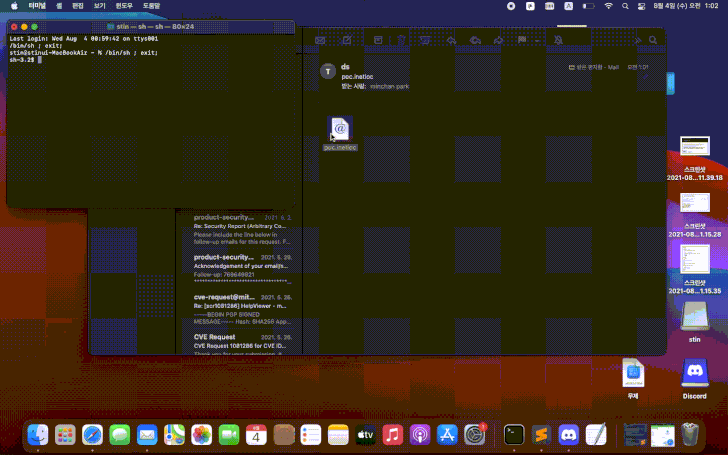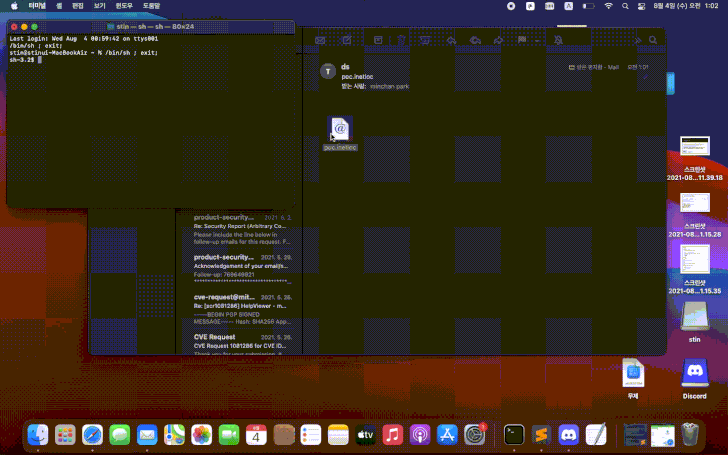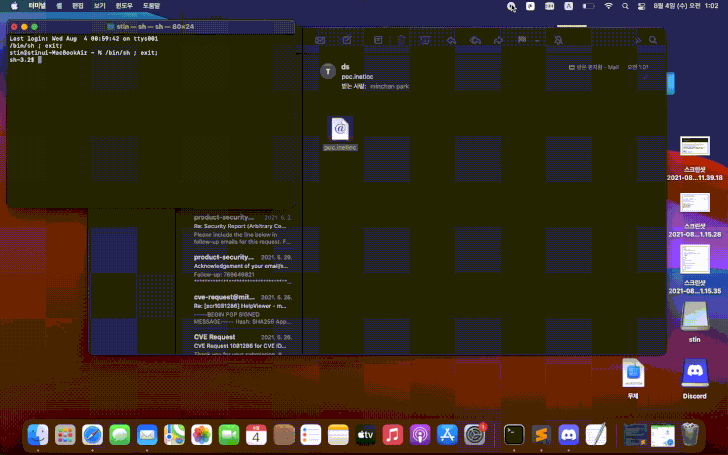
"In newer versions of macOS (Big Sur), the file:// prefix is blocked (in com. apple.generic-internet-location), however, due to problems with the File:// or fIle:// register, checks are bypassed," the expert says.
Although the Minsk resident has already informed Apple about his findings, he has not received a response from the company, and the vulnerability has not yet been fixed.
BleepingComputer has tested the PoC exploit provided by the researcher and confirms that the vulnerability can be used to run arbitrary commands in macOS Big Sur. It is noted that attackers can abuse this benefit, for example, to create malicious email attachments that will launch payloads after opening. Worse, while the .inetloc file with the exploit is not detected by any of the solutions presented on VirusTotal.
Also note that a bookmark was built into M1:
In May 2021, Asahi Linux developer Hector Martin discovered a vulnerability he called M1RACLES (M1SSING Register Access Controls Leak EL0 State). Martin suggested that the vulnerability appeared as a result of Apple's deliberate violation of ARM architecture specifications. As a result of this vulnerability, any two applications can secretly exchange data, bypassing any software protection and isolation tools. The developer also pointed out that the vulnerability cannot be eliminated by software. Despite this, he believes that the vulnerability cannot be used to cause real harm.
What's Your Reaction?